
Cập nhật 58+ về hình nền hack Du học Akina
Spin Bot. Spinbot is by far the most annoying yet easily detectable cheat in CS:GO. Spinbot allows a player to spin around in circles at a rapid pace, this makes it impossible for the opposition to get a shot on the player. The user basically gets a 360-degree FOV, and when combined with an aimbot can one tap anyone instantly.
Network Hack Line Filled Blue 9765385 Vector Art at Vecteezy
1. Type chrome:dino into Chrome's address bar and press Enter. This will display a graphic of a dinosaur with the instruction "Press space to play.". Press the Spacebar on your keyboard to.

How to Hack Someone Line Account Without Them Knowing? Bypass Password & Spy on Line Account
1. The Target: This one is rather obvious, but your target changes what Quickhacks are available to you. For instance, if you're hacking a device, you can't burn out its synapses as it, you know.

Hackers breach Israeli insurance company, steal client data The Times of Israel
Get Instagram support for account access issues including hacked or disabled accounts, problems logging in and impersonation.

Come diventare hacker e quanto si guadagna
Troll your friends and coworkers with Hacker Typer's Hacker Prank Simulator. We make it look like you're coding like a real hacker. Just start typing, we'll do the rest ;)

Pakai Sikit Tapi Line Masih Slow, Ini Cara Nak Trace Wifi Kena Curi & Block Hacker! MASKULIN
Let's start with a simple attack. If we have the username and password that we expect a system to have, we can use Hydra to test it. Here is the syntax: $ hydra -l
Linear Hack Icon From Cyber Outline Collection. Thin Line Hack Vector Isolated On White
So you use fzf, a general-purpose command-line fuzzy finder. It can also do much more than fuzzy-find files. It can used with any list: "files, command history, processes, hostnames, bookmarks, git commits, etc". Super-Pro Hacker Tip: You know that aliases are a great way to make shortcuts to take advantage of fzf's features.

Cara mengubah tampilan CMD ala Hacker Jakatau
BeEF (Browser Exploitation Framework) is yet another impressive tool. It has been tailored for penetration testers to assess the security of a web browser. This is one of the best Kali Linux tools because a lot of users do want to know and fix the client-side problems when talking about web security. 13. Apktool.

Cara Cepat Menjadi Hack Bae (CUMA 6 MENIT) Tutorial Hacker Indonesia! ความรู้ทั่วไปทางธุรกิจ
When using LINE on an iPhone, you can make a backup of your LINE chats on your iCloud account, and it must be linked. You can store your chats, contacts, and attachments all in one place. Let's take a look at how to store LINE chat history via iCloud. Step 1: Open the LINE App on your phone, navigate to Settings → Chats → Chat Backup History.

hacker, Hack, Hacking, Computer, Anarchy, Poster Wallpapers HD / Desktop and Mobile
0:46. Facebook users may have encountered the social media site not working properly on the morning of Super Tuesday. Facebook blamed a "technical issue" for the site being down. "Earlier today, a.

Attacco hacker alla piattaforma Nuls, persi 480.000
Jika akun Line Kamu terhapus atau di-hack oleh orang lain, jangan khawatir, karena ada cara mudah untuk mengembalikannya. Saya sendiri pernah mengalami hal serupa. Untuk mengembalikan akun Line lama yang hilang, kita bisa mengambilnya kembali dengan menggunakan nomor telepon yang terdaftar dalam akun Line kita.

Hacker vs Cracker diferencias de ética MeriStation
Hacked and Fake Accounts. Your account should represent you, and only you should have access to your account. If someone gains access to your account, or creates an account to pretend to be you or someone else, we want to help. We also encourage you to let us know about accounts that represent fake or fictional people, pets, celebrities or.
/hacker-with-laptop-922359280-5c32d4a546e0fb00011bb991.jpg)
What Is Network Hacking and Why Is It a Bad Thing?
The hack underscored how vulnerable government and industry are to even basic assaults on computer networks. Cybersecurity experts said Colonial Pipeline would never have had to shut down its.

The 4 Best Ways to Hack a Website wikiHow
Criminal hackers are now going after phone lines, too One way or another, most phone calls these days involve the internet. Cybersecurity experts say that makes us vulnerable in ways we might not.
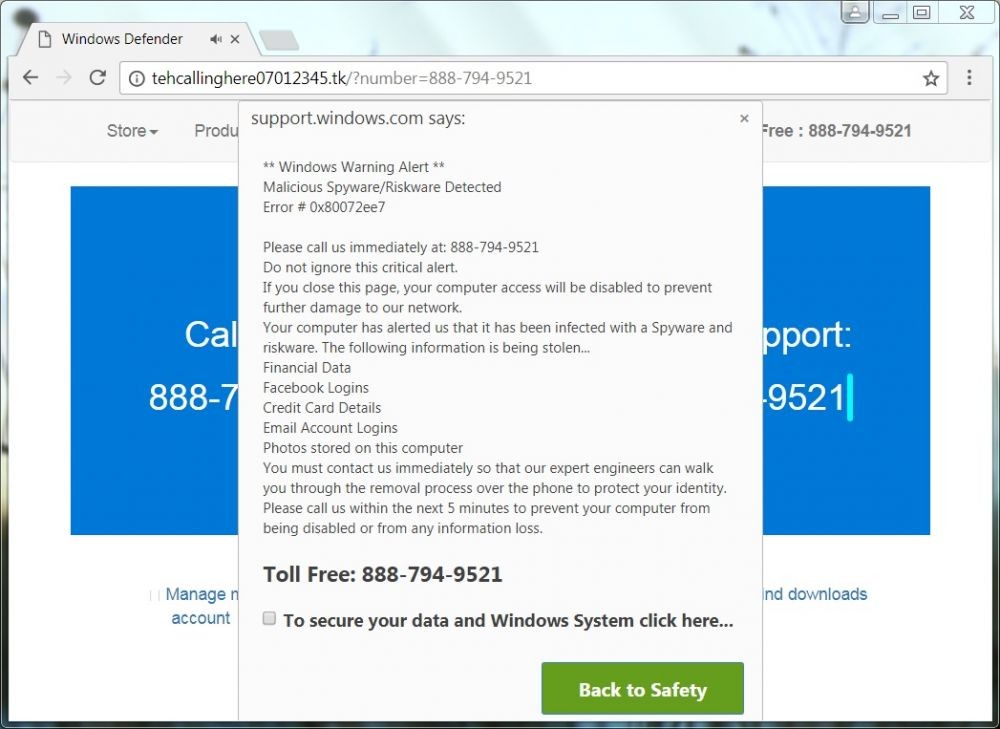
Tanda Komputer Kena Hack, Ini 12 yang Perlu Kamu Waspadai
They create malicious software ("malware") programs that help them gain access to computer networks. Once they have access to a system, black hat hackers can spy on victims' online activities and steal sensitive information to ransom for a price. 2. White hat hackers also infiltrate computer systems, but they do so without malicious intent.
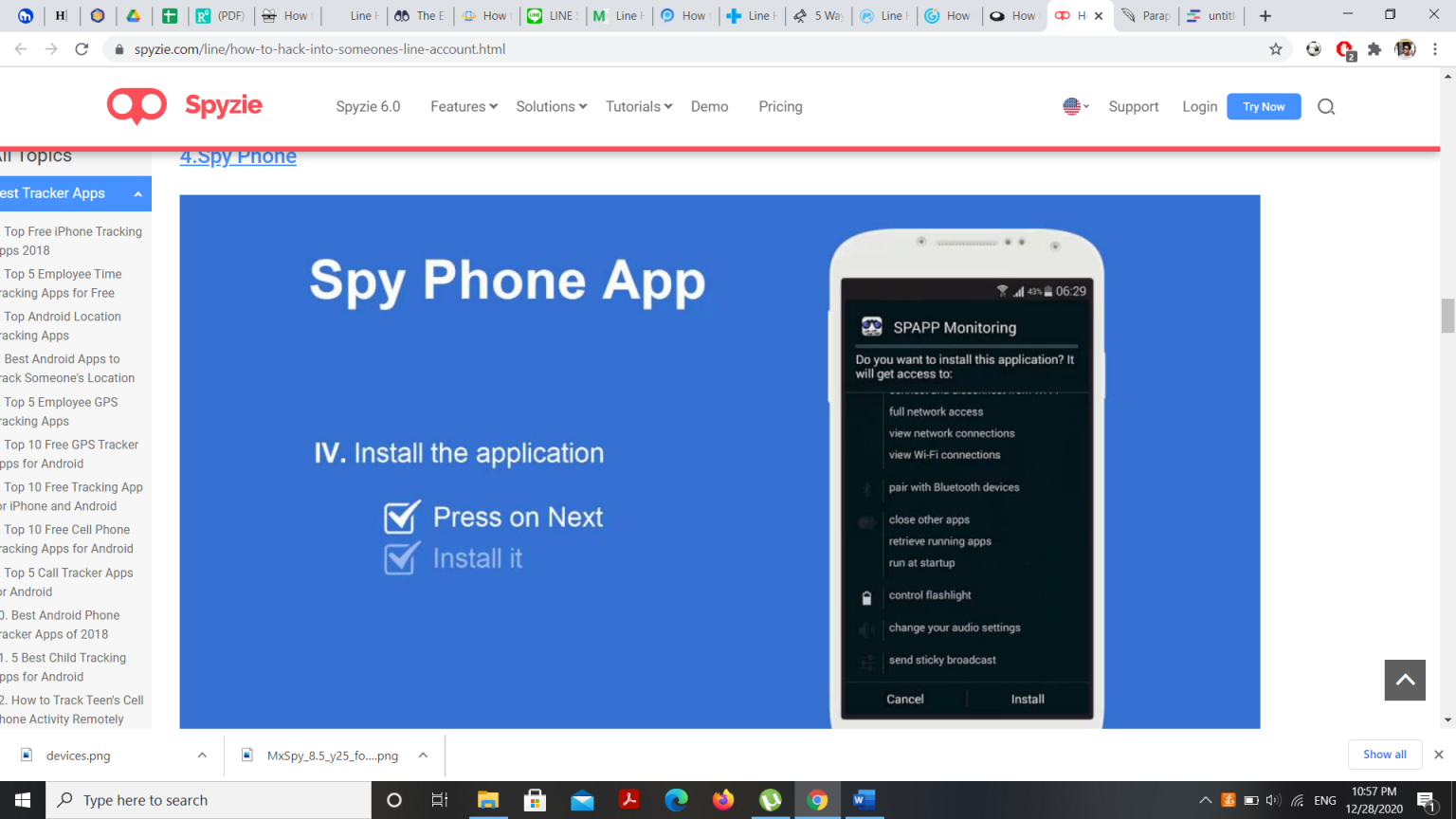
How to Hack Line Messages in 2023 Hack Line Messages MobileSpy
DarkSide [2] [3] On May 7, 2021, Colonial Pipeline, an American oil pipeline system that originates in Houston, Texas, and carries gasoline and jet fuel mainly to the Southeastern United States, suffered a ransomware cyberattack that impacted computerized equipment managing the pipeline. [4] [5] [6] The Colonial Pipeline Company halted all.