
apimswincoreappinitl110.dll Error Windows 11 2 Ways To FIX 2021 YouTube
AppInit_DLLs is a mechanism that allows an arbitrary list of DLLs to be loaded into each user mode process on the system. Upon succesfully execution,\nyou will see the message \"The operation completed successfully.\" Each time the DLL is loaded, you will see a message box with a message of \"Install AppInit Shim DLL was called!\" appear.\nThis.

Malware development persistence part 5. AppInit_DLLs. Simple C++ example.
The AppInit_DLLs value can hold a space separated list of DLLs with full paths, which will be loaded into the process's address space. This is done by using the LoadLibrary() function call during the DLL_PROCESS_ATTACH process of user32.dll; the user32.dll has a special code that traverses through the DLLs and loads them, so this functionality.

Malware development persistence part 5. AppInit_DLLs. Simple C++ example.
The AppInit DLLs are loaded into the process during User32's initialization—that is, while its DllMain function is executing. Developers are explicitly told not to load other DLLs within a DllMain. It can lead to deadlocks and out-of-order loads, which can lead to application crashes. And yet here, the AppInit DLL "feature" does exactly.
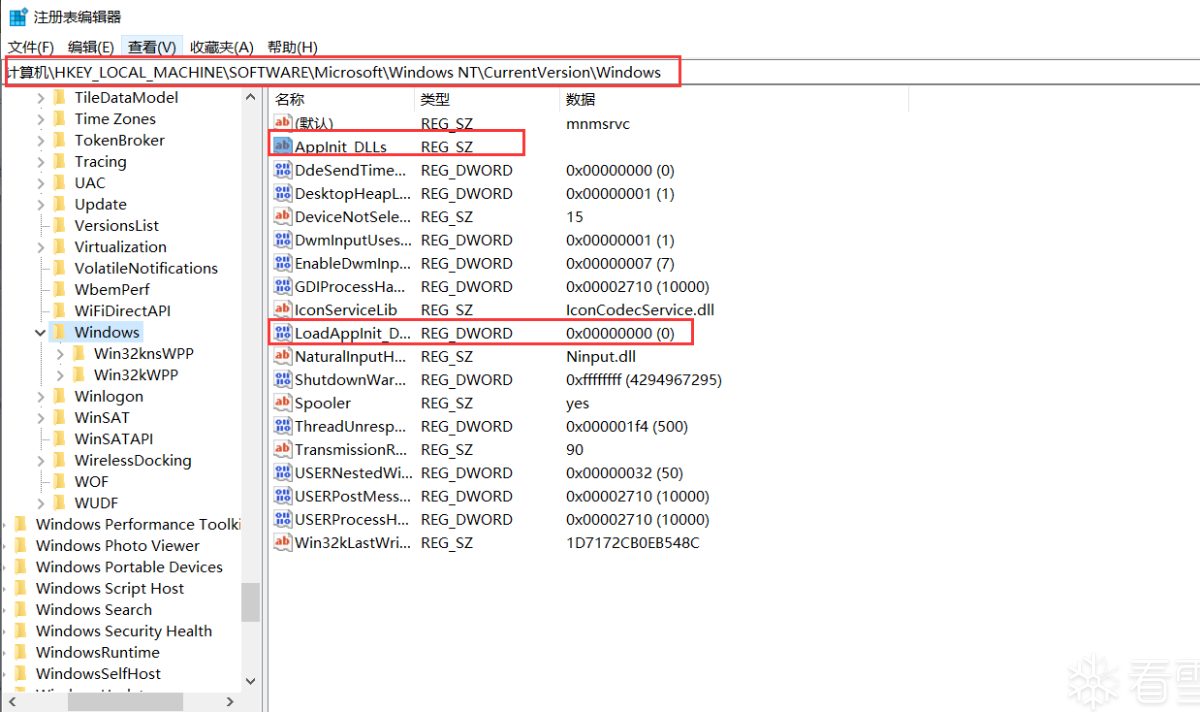
On Vista and later, the AppInit DLLs need to be signed, tho the registry value RequireSignedAppInit_DLLs can be set to 0 which disables this requirement. It's more correct to say that the AppInit_DLL dll is loaded by user32.dll when user32.dll itself is loaded, and that can happen dynamically (delay-load or manual load).

AppInit DLLs · veramine/Detections Wiki · GitHub
Monitor the AppInit_DLLs Registry values for modifications that do not correlate with known software, patch cycles, etc. Adversaries may establish persistence and/or elevate privileges by executing malicious content triggered by AppInit DLLs loaded into processes. Dynamic-link libraries (DLLs) that are specified in the AppInit_DLLs value in the.
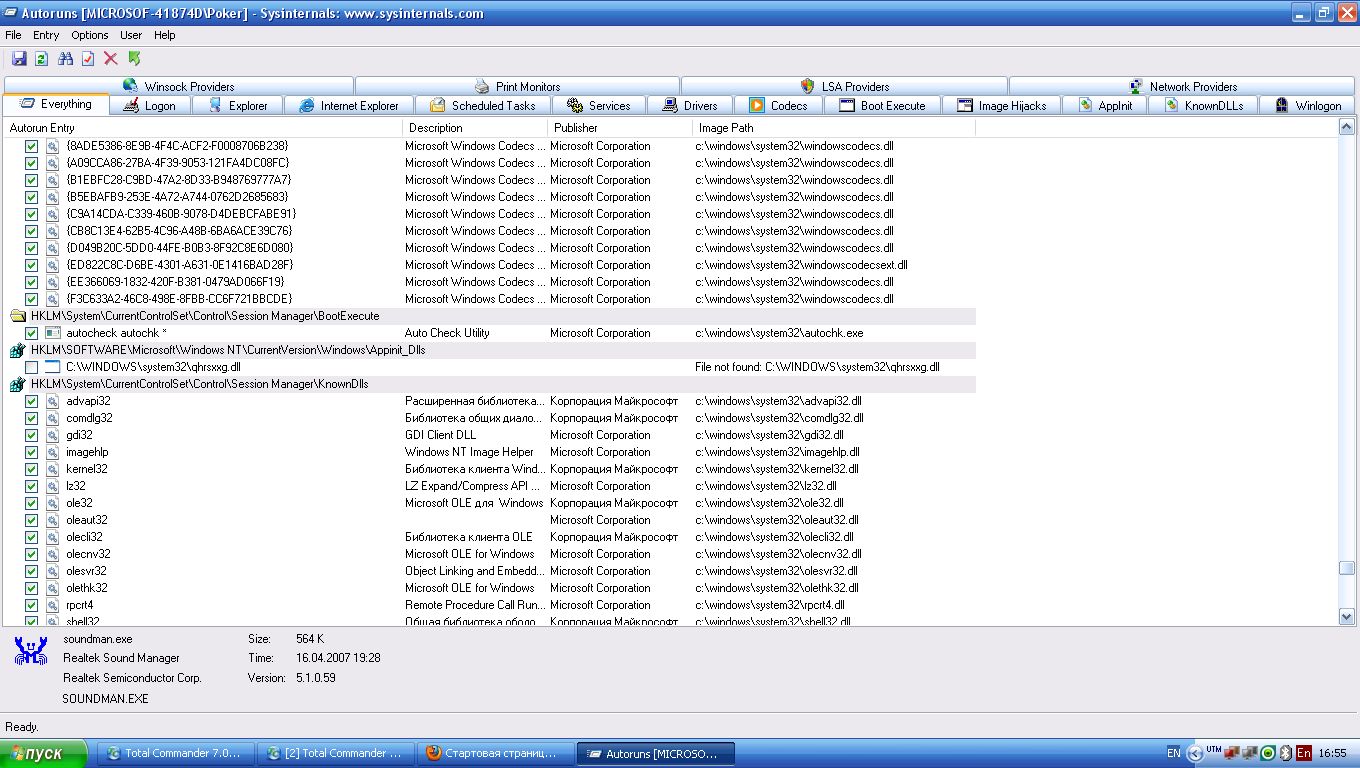
Вирус в HKLM\SOFTWARE\Microsoft\Windows NT\Current Version\Windows\Appinit_Dlls Компьютерная
AppInit_DLLs和安全启动. Windows 8采用 UEFI 和安全启动来提高整体系统完整性,并针对复杂威胁提供强大的保护。. 启用安全启动后,将禁用AppInit_DLLs机制,作为保护客户免受恶意软件和威胁的不妥协方法的一部分。. 请注意,安全启动是 UEFI 协议,而不是Windows 8功能.
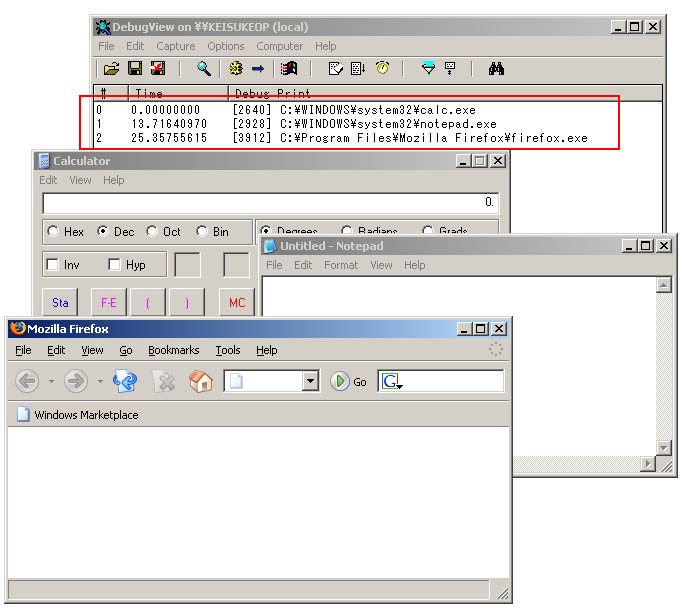
AppInit_DLLs による DLL インジェクション Windows 徹底解説 Web/DB プログラミング徹底解説
AppInit_DLLs is a mechanism that allows an arbitrary list of DLLs to be loaded into each user mode process on the system. Microsoft is modifying the AppInit DLLs facility in Windows 7 and Windows Server 2008 R2 to add a new code-signing requirement. This will help improve the system reliability and performance, as well as improve visibility.

Malware development persistence part 5. AppInit_DLLs. Simple C++ example.
First of all, create "evil" DLL. As usual I will take "meow-meow" messagebox pop-up logic: Then simple logic: changing the registry key AppInit_DLLs to contain the path to the DLL, as a result, evil.dll will be loaded. As you can see, setting the registry key LoadAppInit_DLLs to value 1 is also important.

Windows DLL Injection via AppInit_DLLs Part 2 YouTube
Persistence AppInit DLLs - Meterpreter via Notepad. The utility ListDLLs from Sysinternals can be used to obtain information about the DLL's that are loaded into processes. The following command will retrieve the DLL's that have been loaded into the notepad process which was the selected process for persistence. 1.

Malware development persistence part 5. AppInit_DLLs. Simple C++ example.
The AppInit_DLLs infrastructure loads a predefined set of DLLs to all user-mode processes connected with the User32.dll library (in fact, there are almost no executables, which wouldn't be connected with it). When User32.dll is initialized, it loads the corresponding DLLs, thus performing the DLL injection into processes.

Malware development persistence part 5. AppInit_DLLs. Simple C++ example.
AppInit_DLLs is a mechanism that allows an arbitrary list of DLLs to be loaded into each user mode process on the system. Microsoft is modifying the AppInit DLLs facility in Windows 7 and Windows Server 2008 R2 to add a new code-signing requirement. This will help improve the system reliability and performance, as well as improve visibility.
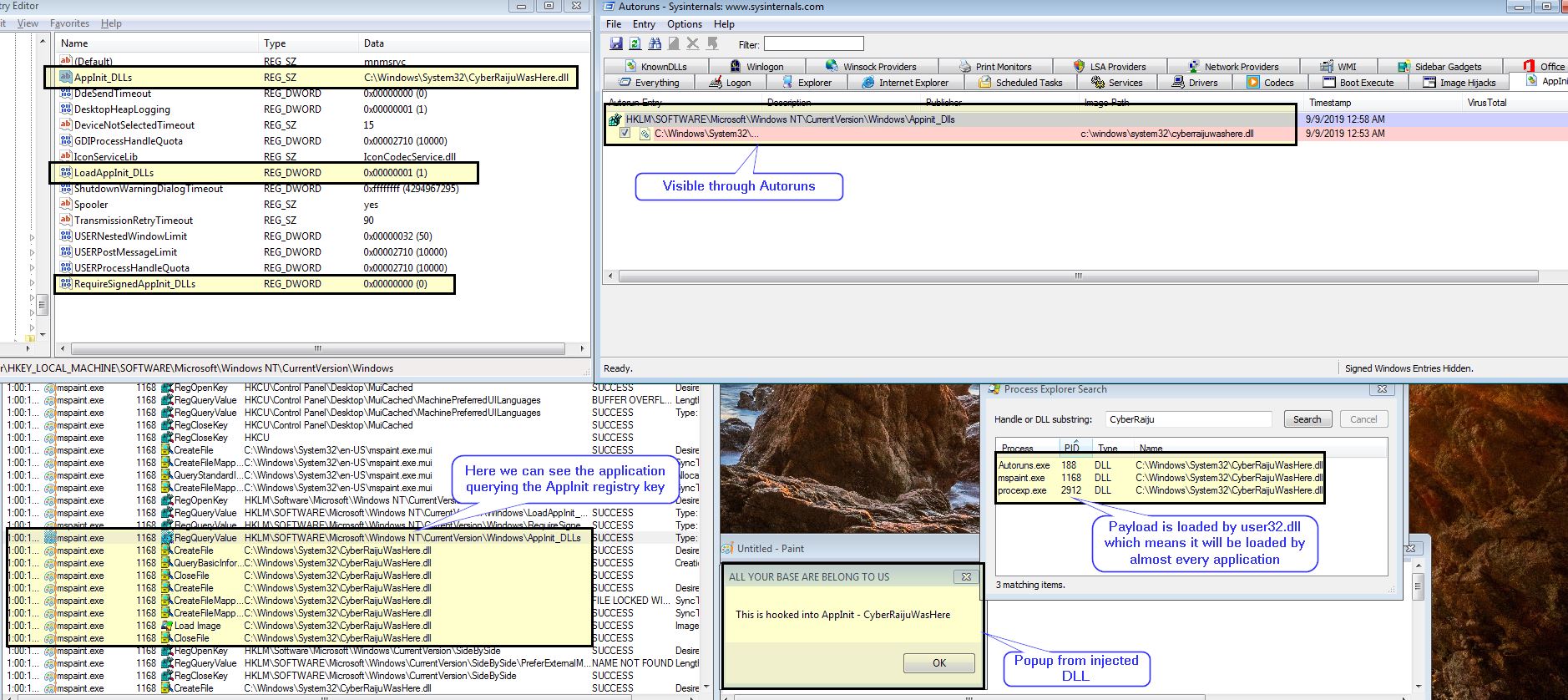
MITRE ATT&CK™ Analysis T1546.010 AppInit DLLs Jai Minton
AppInit_DLLs. Malware can insert the location of their malicious library under the Appinit_Dlls registry key to have another process load their library. Every library under this registry key is loaded into every process that loads User32.dll. User32.dll is a very common library used for storing graphical elements such as dialog boxes.
개발 환경 구성 77. Appinit_Dlls로 구현한 환경 변수 설정 DLL
Using AppInit_DLLs, you can't. Working with the AppInit_DLLs registry value. All the DLLs that are specified in this value are loaded by each Microsoft Windows-based application that is running in the current log on session. I am looking for a way to know from the dll that which application it is calling. A DLL is loaded into the address space.
Inline Hook of a System Call via AppInit_DLLs Part 2 The Hook Todd Cullum Research
The AppInit DLL mechanism is used to load custom code into user-mode processes, allowing for the customization of the user interface and the behavior of Windows-based applications. Attackers who add those DLLs to the registry locations can execute code with elevated privileges, similar to process injection, and provide a solid and constant.

Malware development persistence part 5. AppInit_DLLs. Simple C++ example.
Background on AppInit_DLLs. To quote Microsoft 2: The AppInit_DLLs value is found in the following registry key: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows. All the DLLs that are specified in this value are loaded by each Microsoft Windows-based application that is running in the current log on session.

Cómo reparar errores de appinit_dlls. Error de software espía Silicon Valley Gazette
The AppInit_DLLs infrastructure provides an easy way to hook system APIs by allowing custom DLLs to be loaded into the address space of every interactive application. Applications and malicious software both use AppInit DLLs for the same basic reason, which is to hook APIs; after the custom DLL is loaded, it can hook a well-known system API and.